
Rancher with Docker: Building a Container Management Pipeline from Laptop to Production
Your team just shipped a containerized microservice that works perfectly on everyone’s MacBook but crashes mysteriously in production. The Docker Compose setup that felt so elegant locally has become a liability, and nobody can figure out why the staging environment behaves differently than dev. Sound familiar?
The container revolution promised us consistency—build once, run anywhere. But somewhere between docker-compose up on a developer’s laptop and a Kubernetes deployment manifest in production, that promise breaks down. Your local Redis container runs as root with no resource limits. Your production cluster enforces strict security contexts and memory constraints. The networking model changes completely. Environment variables get injected differently. Suddenly “it works on my machine” isn’t a joke anymore—it’s a systemic problem costing your team hours of debugging and eroding confidence in every deployment.
This gap exists because Docker solves the packaging problem brilliantly but leaves orchestration, scaling, and production-grade management to other tools. Most teams cobble together a patchwork: Docker Desktop locally, maybe some shell scripts for CI, Helm charts they half-understand for Kubernetes, and a prayer that everything connects. Each transition point introduces drift. Each handoff creates an opportunity for configuration mismatches.
Rancher offers a different approach—a unified management plane that spans the entire container lifecycle from local development through production Kubernetes clusters. Instead of treating local and production as separate worlds with incompatible tooling, Rancher creates a consistent abstraction layer that lets you develop, test, and deploy with the same operational model at every stage.
Before diving into how Rancher bridges this gap, let’s examine exactly where traditional Docker workflows fall short.
The Container Management Gap: Why Docker Alone Isn’t Enough
Docker revolutionized software delivery by making containers accessible to every developer. You build an image locally, run it with docker run, and everything works. Then you push to production, and everything breaks.
This isn’t a Docker problem—it’s an architecture problem. Docker excels at packaging and running individual containers. It was never designed to handle the orchestration, scaling, networking, and state management that production systems demand.
The Local-to-Production Disconnect
On your laptop, Docker provides a straightforward mental model: containers are isolated processes with their own filesystems. You map ports, mount volumes, and link containers together. The feedback loop is immediate, and debugging is direct.
Production environments operate on fundamentally different assumptions. Instead of a single machine, you’re managing fleets of nodes. Instead of manual container placement, you need automated scheduling. Instead of static port mappings, you need dynamic service discovery. The skills that make you productive locally don’t transfer to production Kubernetes clusters.
This disconnect manifests in predictable failure patterns:
- Configuration drift: Environment variables, secrets, and resource limits defined in
docker-compose.ymlbear no resemblance to Kubernetes manifests - Networking assumptions: Services that communicate via Docker networks fail when deployed across nodes with different network policies
- Storage mismatches: Local bind mounts don’t translate to persistent volume claims and storage classes
- Resource blindness: Containers that run fine on a 32GB development machine get OOM-killed on production nodes with strict memory limits
Where Rancher Fits
Rancher occupies a unique position in the container ecosystem: it bridges the gap between Docker’s developer experience and Kubernetes’ operational requirements without forcing you to abandon either paradigm.
At the local level, Rancher Desktop provides a Kubernetes cluster that integrates with your existing Docker workflows. You keep using familiar commands and compose files while gaining access to Kubernetes primitives when you need them.
At the infrastructure level, Rancher Server provides centralized management for production Kubernetes clusters across any environment—on-premises, cloud, or hybrid. It abstracts away the differences between EKS, GKE, AKS, and bare-metal installations behind a consistent interface.
💡 Pro Tip: The goal isn’t to eliminate Docker from your workflow. It’s to create a continuous path from
docker buildon your laptop to a production deployment without manually translating between incompatible systems.
Understanding this architectural gap is the first step. The next step is setting up Rancher Desktop to give you local Kubernetes with full Docker compatibility.
Rancher Desktop: Your Local Kubernetes That Speaks Docker
The transition from Docker Desktop to a Kubernetes-native workflow creates friction for teams with established container practices. Rancher Desktop eliminates this friction by providing a local Kubernetes cluster that accepts standard Docker CLI commands, letting you maintain existing workflows while gaining Kubernetes capabilities. This approach proves particularly valuable for organizations standardizing on Kubernetes in production while preserving developer autonomy in local environments.
Installation and Initial Configuration
Rancher Desktop installs as a native application on macOS, Windows, and Linux. On macOS with Homebrew:
brew install --cask rancher
## Verify installation after launching the applicationrdctl versionThe first launch presents a configuration dialog. Select your Kubernetes version—matching your production cluster version prevents compatibility surprises—and choose between containerd and dockerd as your container runtime. The application downloads the necessary components and initializes a single-node Kubernetes cluster running in a lightweight virtual machine.
For teams migrating from Docker Desktop, start with dockerd. This runtime provides full Docker API compatibility, meaning your existing docker build, docker run, and docker compose commands work without modification:
## Confirm Docker CLI connectivitydocker info | grep "Server Version"
## Run a container to verify the full pipelinedocker run --rm alpine:3.19 echo "Rancher Desktop is operational"
## Check that Kubernetes sees your containerskubectl get pods -ARuntime Selection: containerd vs dockerd
The runtime choice affects your development workflow more than performance. dockerd maintains compatibility with Docker-specific features like Docker Compose and the Docker build cache. containerd uses less memory and aligns with how production Kubernetes clusters run containers, making it the preferred choice for teams wanting development environments that closely mirror production behavior.
Understanding the tradeoffs helps inform your decision. The dockerd runtime excels when your team relies heavily on Docker Compose for local service orchestration, uses Docker-specific build features like BuildKit secrets, or maintains shell scripts that invoke Docker commands directly. The containerd runtime suits teams already comfortable with Kubernetes-native tooling, those optimizing for lower resource consumption on developer machines, or organizations enforcing containerd in production and wanting local parity.
Switch runtimes through the Rancher Desktop preferences or via CLI:
## Switch to containerd (requires restart)rdctl set --container-engine containerd
## Switch back to dockerd for Docker Compose compatibilityrdctl set --container-engine moby
## Verify current runtimerdctl list-settings | grep containerEngine💡 Pro Tip: When using containerd, replace
dockercommands withnerdctl. Rancher Desktop aliases this automatically, but scripts referencingdockerdirectly will need updates.
Building Images for Local Kubernetes Deployment
The real power emerges when building images that deploy directly to your local cluster. With dockerd, built images appear in Kubernetes immediately:
## Build an imagedocker build -t myapp:dev ./application
## Deploy to local Kuberneteskubectl create deployment myapp --image=myapp:dev
## Verify the pod uses your local imagekubectl get pods -l app=myapp -o jsonpath='{.items[0].spec.containers[0].image}'With containerd, use nerdctl with the --namespace k8s.io flag to make images available to Kubernetes:
nerdctl --namespace k8s.io build -t myapp:dev ./applicationThis namespace specification ensures the built image lands in the same image store that Kubernetes queries when pulling images for pod creation. Omitting the namespace flag places images in the default nerdctl namespace, invisible to the cluster’s container runtime.
Resource Configuration
Local Kubernetes clusters consume significant resources. Configure limits based on your workload requirements:
## Allocate 4 CPUs and 8GB RAMrdctl set --virtual-machine.memory-in-gb 8rdctl set --virtual-machine.number-cpus 4
## Restart to apply changesrdctl shutdownrdctl startMonitor resource consumption during typical development tasks to find the minimum viable allocation for your workflow. Start conservative—2 CPUs and 4GB RAM handle most single-service development—then increase allocations as your local cluster grows to accommodate additional services. The rdctl CLI provides programmatic control over these settings, enabling teams to script standardized configurations across developer machines.
The local environment now mirrors production Kubernetes while preserving Docker familiarity. However, most applications use Docker Compose for local orchestration—translating those compositions into Kubernetes manifests is where the development-to-production pipeline takes shape.
From Docker Compose to Kubernetes Manifests with Rancher
The gap between your Docker Compose development environment and production Kubernetes manifests represents one of the most frustrating context switches in modern DevOps. You’ve perfected your docker-compose.yml through dozens of iterations, and now you’re staring at the prospect of manually translating every service, volume, and network configuration into Kubernetes resources. Rancher provides a practical bridge that preserves your existing work while enabling a gradual migration path.
The Kompose Foundation
Rancher Desktop ships with kompose, the industry-standard tool for converting Docker Compose files to Kubernetes manifests. Rather than treating this as a one-shot conversion, use it as a starting point for understanding how your services map to Kubernetes primitives.
Consider a typical microservices compose file:
version: "3.8"services: api: build: ./api ports: - "8080:8080" environment: - DATABASE_URL=postgres://db:5432/myapp - REDIS_HOST=cache depends_on: - db - cache db: image: postgres:15 volumes: - pgdata:/var/lib/postgresql/data environment: - POSTGRES_DB=myapp - POSTGRES_PASSWORD=devpassword cache: image: redis:7-alpinevolumes: pgdata:Run the conversion from your Rancher Desktop terminal:
kompose convert -f docker-compose.yml -o k8s-manifests/This generates individual Deployment, Service, and PersistentVolumeClaim files. The output requires refinement—kompose makes conservative assumptions—but you now have a working baseline rather than an empty directory.
Understanding the Conversion Output
Before diving into refinements, examine what kompose produces. Each Docker Compose service becomes a Kubernetes Deployment paired with a Service for network access. Named volumes translate to PersistentVolumeClaims, while the depends_on directive is notably absent from the output—Kubernetes handles service discovery differently, relying on DNS-based resolution rather than startup ordering.
The conversion preserves port mappings and environment variables directly, but exposes them in ways unsuitable for production. Hardcoded database passwords in plain YAML files present obvious security concerns, and the lack of resource constraints means a memory leak in one container could starve others on the same node.
Refining Generated Manifests
The raw conversion misses several production concerns. Kubernetes ConfigMaps and Secrets should replace inline environment variables, and resource limits prevent runaway containers from destabilizing your cluster. Health checks ensure traffic only routes to containers ready to serve requests.
apiVersion: apps/v1kind: Deploymentmetadata: name: api labels: app: apispec: replicas: 2 selector: matchLabels: app: api template: metadata: labels: app: api spec: containers: - name: api image: registry.mycompany.io/api:v1.2.3 ports: - containerPort: 8080 envFrom: - configMapRef: name: api-config - secretRef: name: api-secrets resources: requests: memory: "128Mi" cpu: "100m" limits: memory: "512Mi" cpu: "500m" readinessProbe: httpGet: path: /health port: 8080 initialDelaySeconds: 5 periodSeconds: 10The envFrom directive pulls all keys from the referenced ConfigMap and Secret, keeping sensitive values out of version control while maintaining a clean deployment manifest. Resource requests guarantee minimum allocations for scheduling decisions, while limits cap consumption to protect neighboring workloads.
💡 Pro Tip: Keep your original
docker-compose.ymlfor local development. Rancher Desktop runs both Docker and Kubernetes simultaneously, so developers can choose their preferred workflow while the CI pipeline uses the Kubernetes manifests.
Maintaining Environment Parity
The real value emerges when you establish a consistent structure across environments. Create a Kustomize overlay structure that shares base manifests while allowing environment-specific configuration. This approach lets you define common resource constraints, health checks, and labels once, then customize only what differs between environments.
apiVersion: kustomize.config.k8s.io/v1beta1kind: Kustomizationresources: - api-deployment.yaml - api-service.yaml - db-deployment.yaml - db-service.yaml - cache-deployment.yaml - cache-service.yamlapiVersion: kustomize.config.k8s.io/v1beta1kind: Kustomizationresources: - ../../basepatchesStrategicMerge: - replica-patch.yamlconfigMapGenerator: - name: api-config literals: - DATABASE_URL=postgres://db:5432/myapp - LOG_LEVEL=debugDeploy to your local Rancher Desktop cluster with kubectl apply -k k8s-manifests/overlays/local/, then use the identical base manifests with production overlays when deploying to remote clusters. The configMapGenerator automatically appends a hash suffix to ConfigMap names, triggering rolling updates when configuration values change—a behavior you’d otherwise need to implement manually.
This approach eliminates the “works on my machine” problem at the Kubernetes level. Your local cluster runs the same container images with the same orchestration logic as production—only the configuration values differ. Developers gain confidence that local testing reflects production behavior, while operations teams benefit from manifests already validated through development cycles.
With your manifests structured for multi-environment deployment, the next step is establishing a Rancher Server instance that provides centralized visibility and control across all your clusters.
Deploying Rancher Server for Multi-Cluster Production Management
With local development running smoothly on Rancher Desktop, the next step is establishing a centralized control plane for your production infrastructure. Rancher Server provides a unified management layer that abstracts away the complexity of operating multiple Kubernetes clusters across different environments and cloud providers.
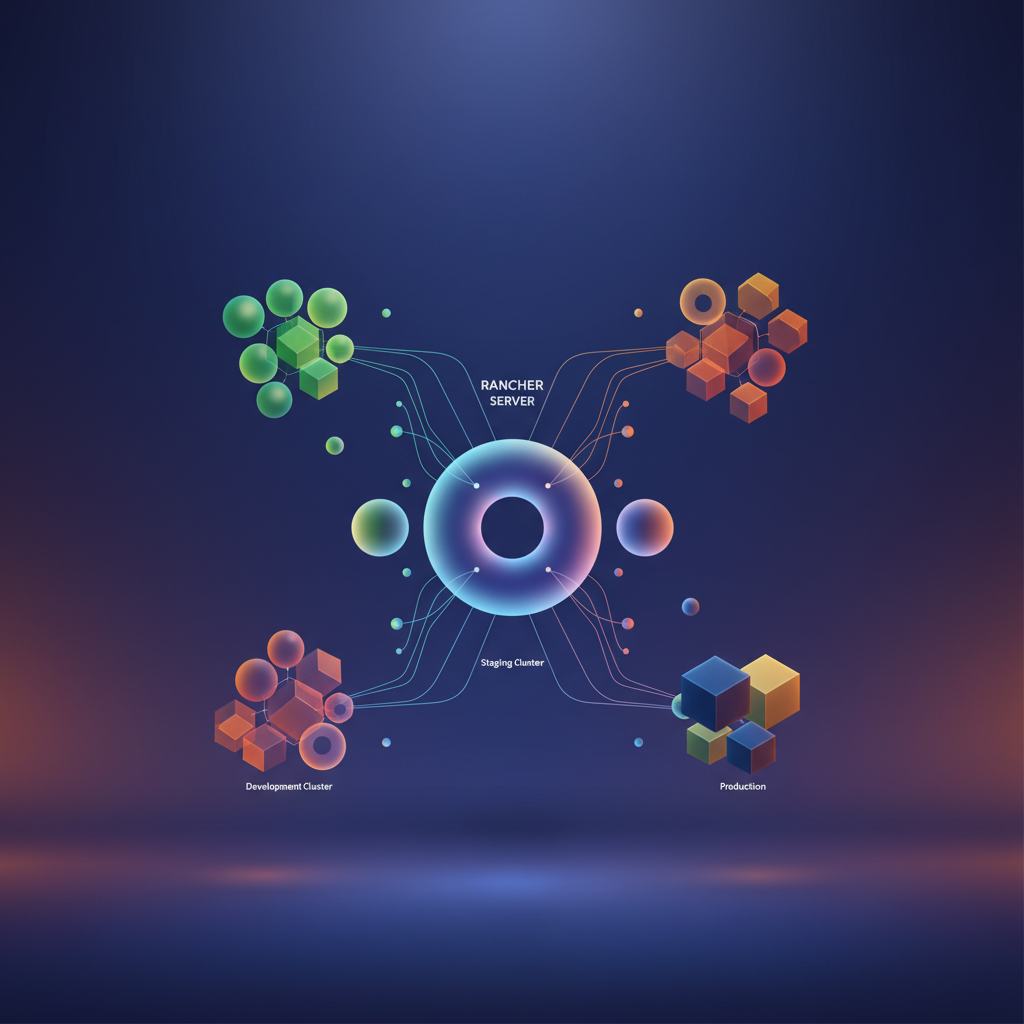
Rancher Server Architecture
Rancher Server runs as a set of containers on any Kubernetes cluster and communicates with downstream clusters through agents. The architecture follows a hub-and-spoke model: the management cluster hosts Rancher itself, while downstream clusters run lightweight agents that establish outbound connections back to the management plane. This design means your production clusters never need inbound connectivity from Rancher—agents phone home through secure WebSocket tunnels.
The management cluster handles authentication, RBAC policies, catalog management, and monitoring aggregation. Downstream clusters remain fully autonomous; if Rancher becomes unavailable, workloads continue running uninterrupted. This separation of concerns ensures that a management plane outage never translates into a production incident for your applications.
For deployment topology, you have several options. Small teams often run Rancher on a dedicated three-node cluster using K3s for minimal overhead. Larger organizations typically deploy Rancher on a hardened RKE2 cluster with dedicated infrastructure. Cloud-native teams might leverage managed Kubernetes services like EKS or GKE as the management cluster foundation, benefiting from the cloud provider’s control plane availability guarantees.
Installing Rancher on Kubernetes
Deploy Rancher using Helm on a dedicated management cluster. Start by installing cert-manager for TLS certificate automation:
## Add required Helm repositorieshelm repo add rancher-stable https://releases.rancher.com/server-charts/stablehelm repo add jetstack https://charts.jetstack.iohelm repo update
## Install cert-manager for certificate managementkubectl create namespace cert-managerhelm install cert-manager jetstack/cert-manager \ --namespace cert-manager \ --version v1.14.4 \ --set installCRDs=true
## Wait for cert-manager podskubectl wait --for=condition=Ready pods --all -n cert-manager --timeout=120s
## Install Rancherkubectl create namespace cattle-systemhelm install rancher rancher-stable/rancher \ --namespace cattle-system \ --set hostname=rancher.example.com \ --set bootstrapPassword=initial-admin-password \ --set replicas=3For production deployments, configure an external load balancer and valid TLS certificates. The hostname value must resolve to your load balancer’s address. Consider using Let’s Encrypt integration for automated certificate renewal, or bring your own certificates from an internal PKI for environments with strict compliance requirements.
💡 Pro Tip: Run at least three Rancher replicas behind a load balancer for high availability. The embedded etcd cluster requires an odd number of nodes for quorum.
Importing Existing Clusters
Once Rancher is running, import your downstream clusters. The import process deploys the Rancher agent, which establishes the management connection:
## Generate import command from Rancher UI or API## This command runs on the downstream cluster
kubectl apply -f https://rancher.example.com/v3/import/gk7xnbc4ctrm2h8w9zswpqjl5.yaml
## Verify agent deploymentkubectl get pods -n cattle-systemkubectl get nodesRancher supports importing any CNCF-conformant Kubernetes cluster: EKS, GKE, AKS, on-premise clusters, or even other Rancher-provisioned clusters. Each imported cluster appears in the Rancher dashboard with full visibility into workloads, nodes, and resource utilization.
The agent deployment creates two primary components in the downstream cluster: the cattle-cluster-agent handles API communication with Rancher, while cattle-node-agent runs as a DaemonSet to provide node-level operations like kubectl shell access and log streaming. Both agents maintain persistent WebSocket connections, automatically reconnecting if network interruptions occur.
Organizing Multi-Cluster Environments
Structure your clusters using Rancher’s project and namespace model. Create projects that map to your deployment stages:
## Using Rancher CLI to create project structurerancher login https://rancher.example.com --token token-abc123:secretvalue
## Create projects for environment isolationrancher projects create --cluster production-us-east --name frontend-teamrancher projects create --cluster production-us-east --name backend-servicesrancher projects create --cluster staging --name integration-testingProjects group namespaces and apply consistent RBAC policies, resource quotas, and network policies across them. Teams access only their designated projects while cluster administrators maintain full visibility. This multi-tenancy model proves especially valuable when multiple teams share cluster infrastructure but require logical isolation for security and resource management purposes.
The centralized dashboard now displays your development, staging, and production clusters in a single view. Deploy applications consistently across environments using Rancher’s catalog system, or leverage the built-in continuous delivery capabilities for automated deployments. Global DNS and multi-cluster application features enable sophisticated deployment patterns like blue-green releases and geographic load balancing across cluster boundaries.
With multi-cluster management operational, the next challenge is automating deployments across these environments. Rancher Fleet provides GitOps-native continuous delivery that scales from a handful of clusters to thousands.
Implementing GitOps Workflows with Rancher Fleet
Rancher Fleet transforms how you manage deployments across multiple clusters by treating Git repositories as the single source of truth. Rather than manually applying manifests or scripting deployments, Fleet continuously reconciles your cluster state with your repository, ensuring what’s committed is what’s running. This declarative approach eliminates configuration drift and provides a complete audit trail of every change made to your infrastructure.
Understanding Fleet’s Architecture
Fleet operates on a simple principle: you define what should exist in your clusters through Git, and Fleet makes it happen. The Rancher server includes Fleet by default, watching your repositories and automatically deploying changes to designated clusters based on rules you define.
At its core, Fleet uses a downstream agent architecture. The Fleet controller runs within Rancher, managing GitRepo resources and generating bundles—packaged sets of Kubernetes manifests ready for deployment. Fleet agents running on each managed cluster pull these bundles and apply them locally, reporting status back to the controller. This pull-based model means managed clusters only need outbound connectivity, simplifying firewall configurations in enterprise environments.
The core abstraction is the GitRepo resource, which tells Fleet where to find your manifests and where to deploy them:
apiVersion: fleet.cattle.io/v1alpha1kind: GitRepometadata: name: webapp-deployments namespace: fleet-defaultspec: repo: https://github.com/acme-corp/webapp-manifests branch: main paths: - /manifests targets: - clusterSelector: matchLabels: env: productionStructuring Repositories for Multi-Environment Deployments
A well-organized Fleet repository separates base configurations from environment-specific overrides. This structure lets you maintain consistency while allowing necessary variations between development, staging, and production:
webapp-manifests/├── base/│ ├── deployment.yaml│ ├── service.yaml│ └── configmap.yaml├── overlays/│ ├── development/│ │ └── fleet.yaml│ ├── staging/│ │ └── fleet.yaml│ └── production/│ └── fleet.yaml└── fleet.yamlEach environment’s fleet.yaml defines targeting rules and any Helm value overrides or Kustomize patches. Fleet natively supports both Helm charts and Kustomize, allowing you to choose the configuration management approach that fits your existing workflows:
defaultNamespace: webapp-prodhelm: releaseName: webapp values: replicas: 5 resources: requests: memory: "512Mi" cpu: "500m" limits: memory: "1Gi" cpu: "1000m"targetCustomizations: - name: production-clusters clusterSelector: matchLabels: env: production region: us-east-1💡 Pro Tip: Use Fleet’s bundle dependencies to ensure infrastructure components deploy before applications. Set
dependsOnin your fleet.yaml to create explicit ordering between deployments.
Automating Rollouts from Commit to Production
Fleet watches your repositories on configurable intervals, but for immediate deployments, configure webhook triggers. When a developer pushes to main, Fleet detects the change and initiates deployment within seconds. This tight feedback loop accelerates development cycles while maintaining the safety guarantees that GitOps provides.
For progressive rollouts, combine Fleet with cluster groups:
apiVersion: fleet.cattle.io/v1alpha1kind: GitRepometadata: name: webapp-staged namespace: fleet-defaultspec: repo: https://github.com/acme-corp/webapp-manifests branch: main targets: - name: canary clusterGroup: canary-clusters - name: production clusterGroup: production-clusters doNotDeploy: trueThis configuration deploys automatically to canary clusters while holding production deployments for manual promotion. After validating the canary deployment through your monitoring stack, remove the doNotDeploy flag or use Rancher’s UI to promote the change. You can also automate this promotion based on metrics thresholds, integrating with tools like Prometheus to gate production rollouts on canary health.
Fleet’s status reporting flows back to Rancher, giving you visibility into deployment state across all clusters from a single dashboard. Failed deployments surface immediately, showing which clusters diverged and why. The bundle status includes detailed error messages, making troubleshooting straightforward even when managing hundreds of clusters.
The GitOps model Fleet enables creates an auditable deployment history—every production change traces back to a specific commit, reviewed and approved through your standard pull request workflow. This traceability proves invaluable when debugging issues or satisfying compliance requirements. Rolling back becomes as simple as reverting a commit, with Fleet automatically reconciling clusters to the previous known-good state.
With Fleet handling your deployment automation, the next challenge becomes understanding what’s happening inside those deployments once they’re running. Effective monitoring and troubleshooting across your entire pipeline requires visibility into both infrastructure and application layers.
Monitoring and Troubleshooting Across the Pipeline
A unified container pipeline demands unified observability. When an issue surfaces, you need identical debugging workflows whether the problem lives on your laptop or in production. Rancher’s integrated monitoring stack, built on Prometheus and Grafana, delivers exactly this consistency—eliminating the cognitive overhead of switching between disparate tools as you trace problems across environments.
Enabling the Monitoring Stack
Rancher Server ships with a one-click monitoring installation that deploys a fully configured Prometheus Operator, Grafana dashboards, and Alertmanager. Navigate to your cluster, select Cluster Tools, and install the Monitoring chart. The default configuration provides comprehensive metrics collection out of the box, but production deployments benefit from tuning retention periods and resource allocations based on cluster size. For programmatic deployment across multiple clusters, use Fleet:
apiVersion: fleet.cattle.io/v1alpha1kind: GitRepometadata: name: monitoring-stack namespace: fleet-defaultspec: repo: https://github.com/myorg/rancher-monitoring-config branch: main paths: - monitoring targets: - clusterSelector: matchLabels: environment: production - clusterSelector: matchLabels: environment: stagingThis configuration deploys identical monitoring across all clusters matching your selectors, ensuring consistent metric collection and alerting rules from staging through production. When you modify alerting thresholds or add new dashboards, Fleet propagates those changes automatically—no manual synchronization required.
Container-Specific Alerts That Matter
Generic CPU and memory alerts generate noise. Container workloads need alerts tuned to their failure modes—pod restart loops, image pull failures, persistent volume issues, and OOMKilled events. The distinction matters: a container hitting 90% memory might be perfectly healthy, while one restarting every five minutes indicates a critical application bug. Configure Alertmanager with rules that capture actual problems:
apiVersion: monitoring.coreos.com/v1kind: PrometheusRulemetadata: name: container-health namespace: cattle-monitoring-systemspec: groups: - name: container-reliability rules: - alert: PodRestartLoop expr: increase(kube_pod_container_status_restarts_total[15m]) > 3 for: 5m labels: severity: warning annotations: summary: "Pod {{ $labels.pod }} restarting frequently"
- alert: ImagePullBackoff expr: kube_pod_container_status_waiting_reason{reason="ImagePullBackOff"} == 1 for: 3m labels: severity: critical annotations: summary: "Image pull failing for {{ $labels.pod }}"Extend these baseline rules with alerts for your specific workload patterns. Stateful applications benefit from alerts on persistent volume capacity, while batch jobs need monitoring for unexpected completion times or failure rates.
Debugging Across Environments
Rancher’s kubectl shell, accessible from any cluster’s dashboard, provides immediate terminal access without context switching. For local development on Rancher Desktop, the same kubectl logs and kubectl exec commands work identically. This symmetry accelerates incident response—you’re not fumbling with unfamiliar tooling when production issues demand immediate attention.
The real power emerges when combining Rancher’s multi-cluster view with Grafana dashboards. Create a single dashboard that accepts cluster as a variable, letting you compare identical metrics across your local Rancher Desktop instance, staging, and production simultaneously. This side-by-side comparison quickly reveals environment-specific anomalies that would otherwise require tedious manual correlation.
💡 Pro Tip: Export your Grafana dashboards as JSON and store them in your Fleet repository. This ensures every environment—including local development—runs the same observability configuration, eliminating “works on my machine” debugging discrepancies.
When container issues occur, this consistency means your debugging muscle memory transfers directly. The same queries, the same dashboards, and the same alert structures apply everywhere. You stop context-switching between tools and start solving problems faster. Engineers who master troubleshooting in development can immediately apply those skills in production incidents.
With observability in place across your entire pipeline, you now have the foundation for a complete container management workflow—from local Docker development through production Kubernetes, managed through a single, coherent toolchain.
Key Takeaways
- Replace Docker Desktop with Rancher Desktop to develop against a real Kubernetes cluster while keeping your Docker CLI workflows intact
- Use Rancher’s manifest conversion tools to migrate Docker Compose projects incrementally rather than attempting a complete rewrite
- Deploy Rancher Server with Helm on your existing cluster and import downstream clusters to create a single management plane for all environments
- Implement Fleet-based GitOps early to ensure every environment stays synchronized with your repository state